Extensive analysis of 200 billion flows across 850 enterprise networks worldwide uncovers high risk from age-old cyber defense weaknesses and leading consumer video sharing application
TEL AVIV, Israel, May 25, 2021 /PRNewswire/ -- Cato Networks, the provider of the world's first SASE platform, announced today the results of its quarterly analysis of global enterprise networks. The Cato Networks SASE Threat Research Report found that popular preconceptions of enterprise security and network usage are often inaccurate. While exotic attacks and nation-states such as Russia and China grab headlines, the most prevalent enterprise cybersecurity risks in Q1 came from unpatched legacy systems, attacks from the US, and consumer applications, such as TikTok.
"Cato's converged SASE solution enables us to pull together security observations with network analysis from live traffic. During Q1, we saw how enterprise security leaders can't focus on newly discovered vulnerabilities at the expense of older, more mundane risks," says Etay Maor, senior director of security strategy at Cato Networks. "Threat actors constantly scan for unpatched, EOL (end of live) and legacy systems, vulnerabilities that are two to nearly 20 years old. And while several governments have raised privacy concerns with TikTok, and ultimately banned this application from their networks and devices, too many enterprise networks continue to carry TikTok flows."
Legacy Security Defenses Fail as Old Exploits Form Most Common Threat
While the industry focuses on exotic attacks - like the SolarWinds breach - the real risk to enterprises comes from older exploits, some as much as 20-years old. "While organizations always need to keep up with the latest security patches, it is also vital to ensure older system and well-known vulnerabilities from years past are monitored and patched as well," says Maor. "Threat actors are attempting to take advantage of overlooked, vulnerable systems."
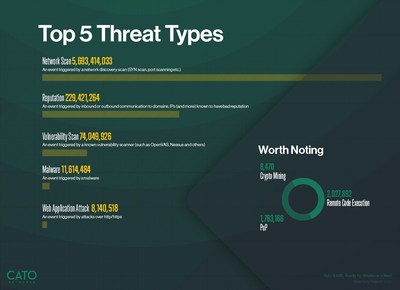
Our research showed that attackers often scanned for end-of-life and unsupported systems. Common Vulnerability and Exposures (CVE) identified by Cato were exploits targeting software, namely vSphere, Oracle WebLogic, and Big-IP, as well as routers with remote administration vulnerabilities.
Patching may address the problem, but enterprises find that staying on top of patching is challenging, and legacy security systems are often insufficient to stop threats. Furthermore, threat actors are constantly changing their signatures and characteristics to avoid detection.
Application Vulnerabilities Expose Many Businesses to Attack
During its analysis of network traffic, Cato identified several security risks. Microsoft Office and Google continue to dominate, but widespread use was seen of remote access software, such as Remote Desktop Protocols (RDP), Virtual Network Computing (VNC), and TeamViewer.
If not properly secured, these applications can be targeted by threat actors with disastrous results, as was made apparent by the recent attacks on the Florida water supply system, Molson Coors, and Colonial Pipeline. "The prevalence of remote access software is troubling from a security perspective. Many attacks on critical infrastructure involved attackers exploiting vulnerabilities and weak passwords in these verry package. If organizations need to run such software, special care must be taken to ensure their security," says Maor.
Enterprise networks also continue to be populated by consumer applications, with the most popular being TikTok that had millions of more flows than Google Mail, LinkedIn, or Spotify. In recent months Cato also saw a significant increase in Robinhood and eToro transactions - likely driven by the recent GameStop-Reddit-Wall Street. The data transmitted to these trading applications surpassed more popular applications such as CNN, The New York Times, and CNBC.
"The increase in consumer applications not only consumes bandwidth but poses a security risk to enterprises," Maor said. "As the type of data flow and applications changes, so does the way in which threat actors exploit vulnerabilities, and in turn, the way enterprises secure their networks must change as well."
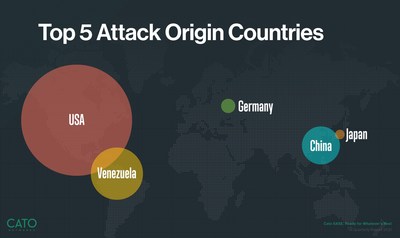
Threats Originate from Countries Other Than Russia or China
To keep in front of attackers, enterprises will often block traffic from certain countries, such as Russia and China. Such an approach is ineffective. Cato's analysis shows that during the first quarter of 2021, most threats did not originate from China or Russia. In fact, more malware attacks originated from the United States than any other country.
"Blocking network traffic to and from 'the usual suspects' may not necessarily make your organization more secure," Maor said. "Threat actors are hosting their Command & Control servers on 'friendly' grounds including the U.S., Germany, and Japan."
Machine Learning Algorithms Spot Network Characteristics of Security Threats
To get a proper understanding of network and cybersecurity trends for its report, Cato Networks analyzed nearly 200 billion network flows from more than 850 enterprises worldwide on the Cato global private backbone between January 1, 2021, and March 31, 2021.
Approximately 16 billion security events were identified and fed to the Cato Threat Hunting System (CTHS). This proprietary machine learning platform identifies threats through contextual network and security analysis. By understanding and identifying the network patterns of cyberattacks, CTHS alerts on security threats often undetected by legacy cybersecurity software.
In all, CTHS identified 181,000 high-risk flows, which led to 19,000 threats verified by the Cato security team. The highlights of this analysis were captured in this report. To learn more, download a copy of The Cato Networks SASE Threat Research Report at https://go.catonetworks.com/SASE-Threat-Research-Report.html.
About Cato Networks
Cato is the world's first?SASE platform, converging?SD-WAN, network security, and?Zero Trust Network Access (ZTNA)?into a global, cloud-native service. Cato optimizes and secures application access for all users and locations. Using?Cato Cloud, customers easily migrate from MPLS to SD-WAN, optimize connectivity to on-premises and cloud applications, enable secure branch Internet access everywhere, seamlessly integrate cloud datacenters into the network, and?connect mobile users with Cato SDP?client and clientless access options. With Cato, the network, and your business, are?ready for whatever's?next.
Infographic - https://mma.prnewswire.com/media/1516354/Cato_Networks_1_Infographic.jpg
Infographic - https://mma.prnewswire.com/media/1516353/Cato_Networks_2_Infographic.jpg