- Fixing Security Flaws Now Takes 8.5 Months-47% Longer Than Five Years Ago
- 15th Annual State of Software Security Study Unveils Five Key Metrics to Benchmark Security Maturity
Veracode, a global leader in application risk management, today launched its 15th edition of the State of Software Security (SoSS) report. The report, based on an extensive dataset of 1.3 million unique applications and 126.4 million raw findings, highlights important trends and offers a new view of software security maturity to improve application risk management practices.
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20250227022178/en/
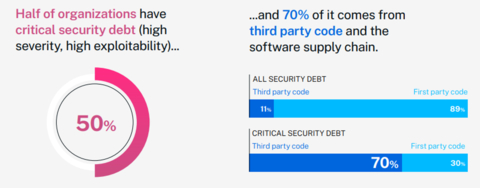
Percentage of Security Debt Across Organizations (Graphic: Business Wire)
The research reveals an alarming increase in the average fix time for security flaws-from 171 days to 252 days over the past five years, and up 327 percent since the report's first volume 15 years ago. Moreover, 50 percent of organizations now carry critical security debt, defined as accumulated flaws left open for longer than a year. The majority of these vulnerabilities originate from third-party code and the software supply chain. Unresolved security debt leaves organizations open to attack, exposing them to reputational, financial, and operational damage.
Chris Wysopal, Chief Security Evangelist at Veracode, said, "The attack surface has become increasingly complicated, particularly in the last couple of years with the explosion of AI engineering. Last year's report found 46 percent of organizations had high-severity security debt. While the year-on-year increase may seem marginal, it is going in the wrong direction. Our investigations provide solid evidence that organizations can drive down debt, but many need help to prioritize which vulnerabilities to tackle first."
Benchmarking Security Performance
Veracode's research also analyzed the distribution of security debt across organizations. While some have almost no debt and others are drowning in it, most fall somewhere in between, with a mix of debt-free and debt-ridden applications.
"The gap between the top 25 percent and bottom 25 percent of organizations is fascinating," Wysopal said. "The results raise the question of which factors account for the marked differences in how organizations manage security debt and what teams can do to tackle it."
Veracode's research pinpoints five key metrics that indicate security maturity and predict an organization's ability to systematically reduce risk: flaw prevalence, fix capacity, fix speed, debt prevalence, and open-source debt. The report explains each metric's importance and reveals the parameters that determine whether an organization is "leading" or "lagging."
- Flaw prevalence: Leading organizations have flaws in fewer than 43 percent of applications, while lagging organizations exceed 86 percent.
- Fix capacity: Leaders resolve over 10 percent of flaws monthly, whereas laggards address less than 1 percent.
- Fix speed: Top performers remediate half of flaws in five weeks; lower-performing organizations take longer than a year.
- Security debt prevalence: Less than 17 percent of applications in leading organizations carry security debt, compared with more than 67 percent in lagging ones.
- Open-source debt: Leading organizations keep open-source critical debt under 15 percent, while 100 percent of critical debt is open source in lagging organizations.
Wysopal said, "The research provides a helpful framework for organizations to assess their security maturity. This enables them to understand specific factors contributing to security debt, gauge each metric's importance, and benchmark their own performance against similar organizations. We offer in-depth recommendations from our experts and leading organizations on how to improve."
Cyber Regulations Drive Positive Behaviors, Boosting Application Security
On a positive note, Veracode's research found the rate of applications passing the Open Worldwide Application Security Project (OWASP) Top 10 has increased by 63 percent over the past five years, and more than doubled in 15 years. New cybersecurity regulations in 2024, like the U.S. Securities and Exchange Commission (SEC) ruling and E.U. Cyber Resilience Act, have contributed to this trend as software vendors take a more disciplined approach to risk management.
A New View of Security Maturity
Veracode's new view of software security maturity emphasizes the need for enterprises to take a strategic, context-driven approach to managing the most urgent and exploitable risks. The report recommends two key focus areas for organizations. First, organizations must enhance visibility and integration across the entire software development life cycle, using automation and feedback loops to prevent new security flaws. Second, they should prioritize correlating and contextualizing security findings in a single view, allowing them to efficiently address their security backlog and reduce the highest risks with the least effort.
Wysopal added, "Tools like Application Security Posture Management enable security professionals and development teams to prioritize and make informed decisions by pinpointing what's exploitable, reachable, and urgent."
As organizations navigate an increasingly complex threat landscape, prioritizing security maturity is essential. Veracode's research provides a roadmap for organizations to benchmark and improve their security posture. By addressing security debt and leveraging the best tools and practices, businesses can enhance resilience, reduce risk, and comply with evolving cybersecurity regulations.
The full State of Software Security 2025 report is available to download on the Veracode website. A blog outlining the key findings from the report is also available to read.
About the State of Software Security Report
The Veracode State of Software Security 2025 is the 15th volume of the report. It analyzed data from companies of all sizes, commercial software suppliers, software outsourcers, and open-source projects. The report contains findings about applications that were subjected to static analysis, dynamic analysis, software composition analysis, and/or manual penetration testing through Veracode's cloud-based platform. Specifically, the data comes from:
- 1.3M unique applications with 126.4M raw findings
- 107.4M findings identified via SAST scans
- 3.9M findings identified via DAST scans
- 15M findings identified via Software Composition Analysis
About Veracode
Veracode is a global leader in Application Risk Management for the AI era. Powered by trillions of lines of code scans and a proprietary AI-assisted remediation engine, the Veracode platform offers adaptive software security and is trusted by organizations worldwide to build and maintain secure software from code creation to cloud deployment. Thousands of the world's leading development and security teams use Veracode every second of every day to get accurate, actionable visibility of exploitable risk, achieve real-time vulnerability remediation, and reduce their security debt at scale. Veracode is a multi-award-winning company offering capabilities to secure the entire software development life cycle, including Veracode Fix, Static Analysis, Dynamic Analysis, Software Composition Analysis, Container Security, Application Security Posture Management, Malicious Package Detection, and Penetration Testing.
Learn more at www.veracode.com, on the Veracode blog, and on LinkedIn and X.
Copyright 2025 Veracode, Inc. All rights reserved. Veracode is a registered trademark of Veracode, Inc. in the United States and may be registered in certain other jurisdictions. All other product names, brands or logos belong to their respective holders. All other trademarks cited herein are property of their respective owners.
View source version on businesswire.com: https://www.businesswire.com/news/home/20250227022178/en/
Contacts:
For more information, please contact:
Katy Gwilliam
kgwilliam@veracode.com
